Certified Red Team Professional Lab Objective:
The importance of Active Directory in an enterprise cannot be stressed enough. Used by more than 90% of Fortune 1000 companies, the all-pervasive AD is the focal point for adversaries. Still, when it comes to AD security, there is a large gap of knowledge which security professionals and administrators struggle to fill. Over the years, we have taught numerous professionals in real world trainings on AD security and always found that there is a lack of quality material and specially, dearth of practice lab where one can practice AD attacks in a controlled environment.

Attacking and Defending Active Directory (Certified Red Team Professional) Lab is designed to provide a platform for security professionals to understand, analyze and practice threats and attacks in a modern Active Directory environment. The lab is beginner friendly and comes with a complete video course and lab manual. The course and the lab are based on our years of experience of making and breaking Windows and AD environments and teaching security professionals.
The lab is tightly integrated with the course and is designed as a practice lab rather than a challenge lab. We cover topics like AD enumeration, trusts mapping, domain privilege escalation, domain persistence, Kerberos based attacks (Golden ticket, Silver ticket and more), ACL issues, SQL server trusts, Defenses and bypasses of defenses.
What’s Included

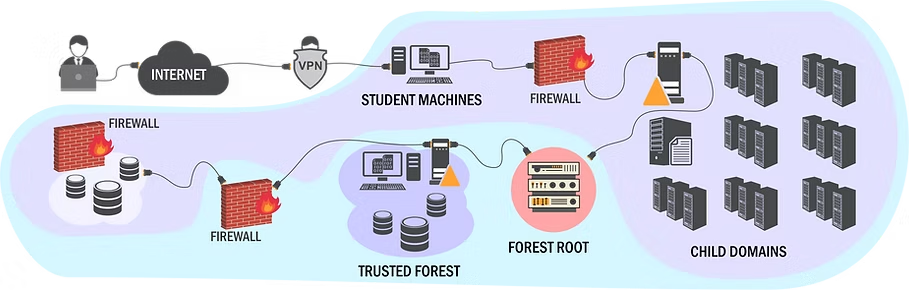
Access to a lab environment (One/Two/Three months) with updated Server 2022 machines. Lab can be accessed using a web browser or VPN.
A ready to use student VM in the cloud that has all the tools pre-installed.
Life time access to all the learning material (including course updates).
14+ hours of video course
Course slides.
Lab manual.
Walk-through videos.
One Certification Exam attempt for Certified Evasion Techniques Professional (CETP) certification.
Support on email and Discord.
What will you Learn?
The Attacking and Defending Active Directory Lab enables you to:
- Practice various attacks in a fully patched realistic Windows environment with Server 2022 and SQL Server 2017 machine.
- Multiple domains and forests to understand and practice cross trust attacks.
- Learn and understand concepts of well-known Windows and Active Directory attacks.
- Learn to use Windows as an attack platform and using trusted features of the OS like .NET, PowerShell and others for attacks.
- Bypassing defenses like Windows Defender, Microsoft Defender for Endpoint (MDE) and Microsoft Defender for Identity (MDI).

Prerequisites for the course
- Basic understanding of Active Directory.
- Ability to use command line tools on Windows.
Purchase On-Demand Lab
30 DAYS LAB ACCESS
+
LIFE TIME ACCESS TO
COURSE MATERIAL
+
ONE CERTIFICATION
EXAM ATTEMPT
$249
60 DAYS LAB ACCESS
+
LIFE TIME ACCESS TO
COURSE MATERIAL
+
ONE CERTIFICATION
EXAM ATTEMPT
$379
90 DAYS LAB ACCESS
+
LIFE TIME ACCESS TO
COURSE MATERIAL
+
ONE CERTIFICATION
EXAM ATTEMPT
$499
30 DAYS LAB EXTENSION
+
ONE COMPLEMENTARY
EXAM ATTEMPT
$199
EXAM REATTEMPT
$99
Exam Reattempt is only for existing or past students of this course who have already purchased this course in the past.
Certificate Renewal - Only For Existing CRTP Certified Student
30 DAYS LAB ACCESS
FOR CERT RENEWAL
$149
ADDITIONAL
RENEWAL EXAM
$29
Add to cart
Intermediate
[March 2025] Bootcamp CRTE : Attacking and Defending Active Directory: Advanced Edition
A deep dive into Red Teaming – Practice attacks with focus on OpSec, Living Off the Land and bypassing security controls like MDI, WDAC and more in a secure multi-forest active directory lab environment.Earn the CRTE certification.
Starts: 8th March 2025
Duration: 4 weeks
Recordings of live sessions included!
Terms of Purchase and Use:
You can start your lab access anytime within 90 days (180 days in case you have purchased the lab on Diwali / Black Friday sale) of purchase
One Certification Exam attempt is included in the pricing. Additional exam attempts will be $99 each
Once connected over VPN, consider the lab to be a hostile environment and you are responsible for your computer’s security
The above lab is a shared environment and certain pre-specified machines will be off-limits
If you want a dedicated lab just for yourself, please use the form in the Contact-Us tab
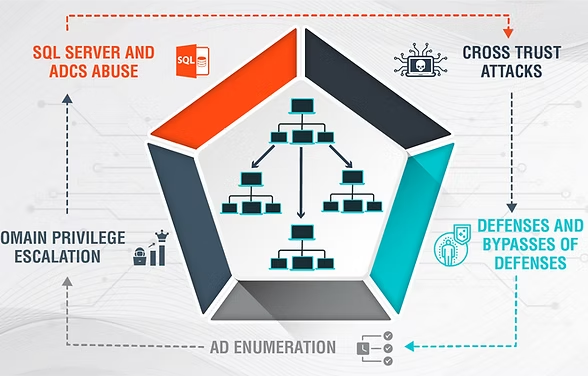
23 Learning Objectives, 59 Tasks, >120 Hours of Torture
I. Active Directory Enumeration
Use scripts, built-in tools and Active Directory module to enumerate the target domain.
Understand and practice how useful information like users, groups, group memberships, computers, user properties etc. from the domain controller is available to even a normal user.
Understand and enumerate intra-forest and inter-forest trusts. Practice how to extract information from the trusts.
Enumerate Group policies.
Enumerate ACLs and learn to find out interesting rights on ACLs in the target domain to carry out attacks.
Learn to use BloodHound and understand its applications in a red team operation.
II. Offensive PowerShell Tradecraft
Learn how PowerShell tools can still be used for enumeration.
Learn to modify existing tools to bypass Windows Defender.
Bypass PowerShell security controls and enhanced logging like System Wide Transcription, Anti Malware Scan Interface (AMSI), Script Blok Logging and Constrained Language Mode (CLM)
III. Offensive .NET Tradecraft
Learn how to modify and use .NET tools to bypass Windows Defender and Microsoft Defender for Endpoint (MDE).
Learn to use .NET Loaders that can run assemblies in-memory.
IV. Local Privilege Escalation
Learn and practice different local privilege escalation techniques on a Windows machine.
Hunt for local admin privileges on machines in the target domain using multiple methods.
Abuse enterprise applications to execute complex attack paths that involve bypassing antivirus and pivoting to different machines.
V. Domain Privilege Escalation
Learn to find credentials and sessions of high privileges domain accounts like Domain Administrators, extracting their credentials and then using credential replay attacks to escalate privileges, all of this with just using built-in protocols for pivoting.
Learn to extract credentials from a restricted environment where application whitelisting is enforced. Abuse derivative local admin privileges and pivot to other machines to escalate privileges to domain level.
Understand the classic Kerberoast and its variants to escalate privileges.
Enumerate the domain for objects with unconstrained delegation and abuse it to escalate privileges.
Find domain objects with constrained delegation enabled. Understand and execute the attacks against such objects to escalate privileges to a single service on a machine and to the domain administrator using alternate tickets.
Learn how to abuse privileges of Protected Groups to escalate privileges
VI. Domain Persistence and Dominance
Abuse Kerberos functionality to persist with DA privileges. Forge tickets to execute attacks like Golden ticket, Silver ticket and Diamond ticket to persist.
Subvert the authentication on the domain level with Skeleton key and custom SSP.
Abuse the DC safe mode Administrator for persistence.
Abuse the protection mechanism like AdminSDHolder for persistence.
Abuse minimal rights required for attacks like DCSync by modifying ACLs of domain objects.
Learn to modify the host security descriptors of the domain controller to persist and execute commands without needing DA privileges.
VII. Cross Trust Attacks
Learn to elevate privileges from Domain Admin of a child domain to Enterprise Admin on the forest root by abusing Trust keys and krbtgt account.
Execute intra-forest trust attacks to access resources across forest.
Abuse SQL Server database links to achieve code execution across forest by just using the databases.
VIII. Abusing AD CS
Learn about Active Directory Certificate Services and execute some of the most popular attacks.
Execute attacks across Domain trusts to escalate privileges to Enterprise Admins.
IX. Defenses and bypass – MDE EDR
Learn about Microsoft’s EDR – Microsoft Defender for Endpoint.
Understand the telemetry and components used by MDE for detection.
Execute an entire chain of attacks across forest trust without triggering any alert by MDE.
Use Security 365 dashboard to verify MDE bypass.
X. Defenses and bypass – MDI
Learn about Microsoft Identity Protection (MDI).
Understand how MDI relies on anomaly to spot an attack.
Bypass various MDI detections throughout the course.
XI. Defenses and bypass – Architecture and Work Culture Changes
Learn briefly about architecture and work culture changes required in an organization to avoid the discussed attacks. We discuss Temporal group membership, ACL Auditing, LAPS, SID Filtering, Selective Authentication, credential guard, device guard, Protected Users Group, PAW, Tiered Administration and ESAE or Red Forest
XII. Defenses – Monitoring
Learn about useful events logged when the discussed attacks are executed.
XIII. Defenses and Bypass – Deception
Understand how Deception can be effective deployed as a defense mechanism in AD.
Deploy decoy user objects, which have interesting properties set, which have ACL rights over other users and have high privilege access in the domain along with available protections.
Deploy computer objects and Group objects to deceive an adversary.
Learn how adversaries can identify decoy objects and how defenders can avoid the detection.
Certified Red Team Professional (CRTP)
The Certified Red Team Professional is a completely hands-on certification. To be certified, a student must solve practical and realistic challenges in our fully patched Windows infrastructure labs containing multiple Windows domains and forests. The certification challenges a student to compromise Active Directory by abusing features and functionalities without relying on patchable exploits. Students will have 24 hours for the hands-on certification exam.
A certification holder has the skills to understand and assess security of an Active Directory environment.

In case you have to retake the exam, a re-attempt fee of $99 is applicable. There is a cool down period of one month before a student can appear in the exam again. The student will get an exam environment from the pool of our different exam labs. After total 3 attempts (1 included with the lab and two additional attempts), a student must wait for a cool down period of 6 months.
Certificate Expiry and Renewal
Exam Structure
The students are provided access to an individual Windows environment, which is fully patched and contains the latest Windows operating systems with configurations and privileges like a real enterprise environment.
To be successful, students must solve the challenges by enumerating the environment and carefully constructing attack paths. The students will need to understand how Windows domains work, as most exploits cannot be used in the target network.
At the end of the exam, students need to submit the detailed solutions to challenges along with practical mitigations.
Certificate Benefits
Over the years, CRTP has been established itself as an industry-recognized certification as a Red Team certification for beginners. CRTP is a prerequisite for numerous job postings and is recognized by several industrial bodies and governments across the globe.
A certificate holder has demonstrated the understanding of AD security. She can identify and enumerate interesting information and execute variety of attack techniques like local and domain privilege escalation, persistence, trust abuse and antivirus evasion with minimal chances of detection.
The certificate holder is ready for the next level that is Certified Red Team Expert: https://www.alteredsecurity.com/redteamlab
Nikhil: Founder of Altered Security, BlackHat USA Trainer, DEF CON Speaker

Nikhil Mittal is a hacker, infosec researcher, speaker and enthusiast. His area of interest includes red teaming, Azure and active directory security, attack research, defense strategies and post exploitation research. He has 15+ years of experience in red teaming.
He specializes in assessing security risks at secure environments that require novel attack vectors and “out of the box” approach. He has worked extensively on Azure AD, Active Directory attacks, defense and bypassing detection mechanisms.
Nikhil has trained more than 10000 security professionals in private trainings and at the world’s top information security conferences.He has spoken/trained at conferences like DEF CON, BlackHat, BruCON and more.
He is the founder of Altered Security – a company focusing on hands-on enterprise security learning – https://www.alteredsecurity.com/
Purchase On-Demand Lab
30 DAYS LAB ACCESS
+
LIFE TIME ACCESS TO
COURSE MATERIAL
+
ONE CERTIFICATION
EXAM ATTEMPT
$249
60 DAYS LAB ACCESS
+
LIFE TIME ACCESS TO
COURSE MATERIAL
+
ONE CERTIFICATION
EXAM ATTEMPT
$379
90 DAYS LAB ACCESS
+
LIFE TIME ACCESS TO
COURSE MATERIAL
+
ONE CERTIFICATION
EXAM ATTEMPT
$499
30 DAYS LAB EXTENSION
+
ONE COMPLEMENTARY
EXAM ATTEMPT
$199
EXAM REATTEMPT
$99
Exam Reattempt is only for existing or past students of this course who have already purchased this course in the past.
Certificate Renewal - Only For Existing CRTP Certified Student
30 DAYS LAB ACCESS
FOR CERT RENEWAL
$149
ADDITIONAL
RENEWAL EXAM
$29
Add to cart
Intermediate
[March 2025] Bootcamp CRTE : Attacking and Defending Active Directory: Advanced Edition
A deep dive into Red Teaming – Practice attacks with focus on OpSec, Living Off the Land and bypassing security controls like MDI, WDAC and more in a secure multi-forest active directory lab environment.Earn the CRTE certification.
Starts: 8th March 2025
Duration: 4 weeks
Recordings of live sessions included!

Terms of Purchase and Use:
You can start your lab access anytime within 90 days (180 days in case you have purchased the lab on Diwali / Black Friday sale) of purchase
You need a Google account to access the lab portal adlab.enterprisesecurity.io
One Certification Exam attempt is included in the pricing. Additional exam attempts will be $99 each
Once connected over VPN, consider the lab to be a hostile environment and you are responsible for your computer’s security
The above lab is a shared environment and certain pre-specified machines will be off-limits
If you want a dedicated lab just for yourself at extra cost, please use the form in the Contact-Us tab