Summary
With the introduction of Tamper Protection, it has now become harder to disable Defender settings as an adversary. This is due to the fact that Tamper Protection and other Defender registry settings are protected by a Kernel-mode driver called WdFilter.sys.
During my research I found it possible to abuse SYSTEM / TrustedInstaller privileges to tamper WdFilter settings and unload the kernel minidriver to disable Tamper protection and other Defender components. This also affects Microsoft’s Defender for Endpoint (MDE), blinding MDE of telemetry and activity performed on a target.
I have created a POC called Disable-TamperProtection showcasing this bypass to disable WdFilter, Tamper Protection, Real-time protection (AMSI) and reinstate them back. A sample test against a target Server 2022 MDE testlab instance can be found below.
The POC can be found on GitHub here: https://github.com/AlteredSecurity/Disable-TamperProtection
NOTE: Administrative privileges are required to run the POC and technique.
Description
Tamper Protection in Windows Security helps prevent malicious apps from changing important Microsoft Defender Antivirus settings, including Real-time protection and cloud-delivered protection. With the introduction of Tamper Protection, it is not possible to disable Defender settings using commands such as:
Set-MpPreference -DisableRealtimeMonitoring $true
To disable Tamper Protection via registry, the registry subkey – TamperProtection located at HKLM\SYSTEM\CurrentControlSet\Services\WinDefend should be set from 5 to 0/4.
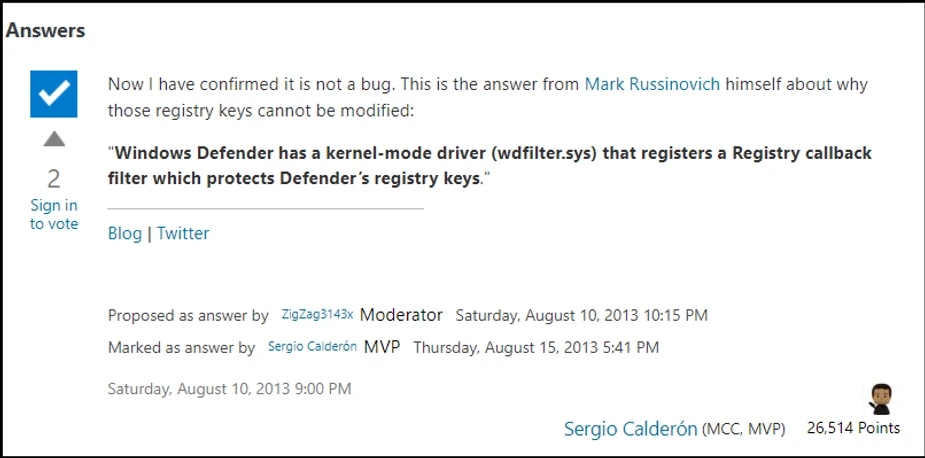
It is not possible to modify registry subkey values at
HKLM\SYSTEM\CurrentControlSet\Services\WinDefend even using SYSTEM / TrustedInstaller privileges because “Windows Defender has a kernel-mode driver (WdFilter.sys) that registers a Registry callback filter which protects Defender’s registry keys.”