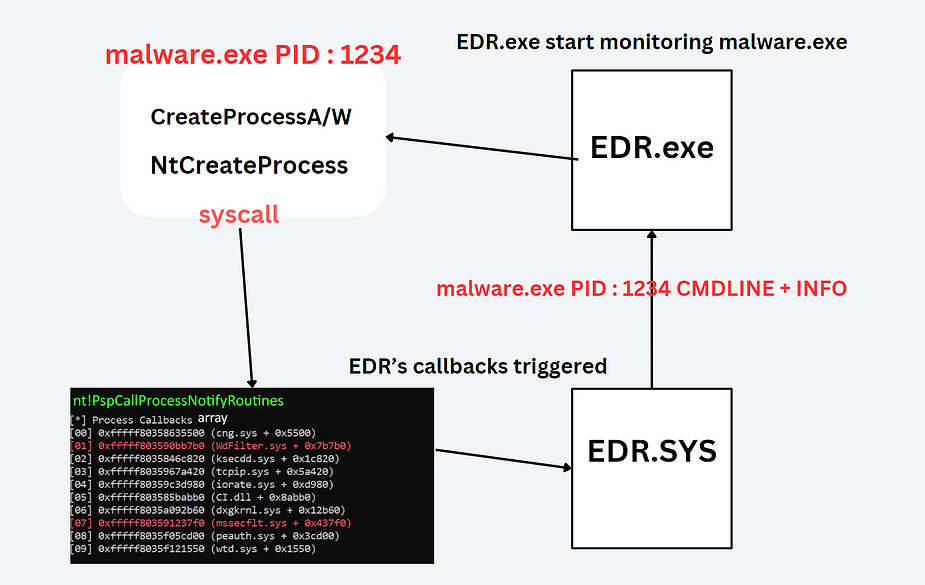
Intro In the ever-evolving landscape of cybersecurity, the race between attackers and defenders is relentless. Security mechanisms, particularly those at the kernel level, are designed to provide robust protection against sophisticated threats. However, as attackers continuously devise new methods to bypass these defenses, the hunters—our trusted Endpoint Detection and Response (EDR) systems—can themselves become the hunted. This blog delves into a chilling demonstration of how a signed rootkit, can leverage the PsSetCreateProcessNotifyRoutine function to cripple EDR processes. By registering a custom callback, this rootkit effectively blindsides security defenses, preventing critical EDR processes from starting and leaving the system vulnerable to undetected malicious activities. Join us as we explore this advanced threat tactic, emphasizing the urgent need for fortified kernel-level protections to maintain the integrity and effectiveness of our security infrastructure. How EDR is Detecting Processes once created ? When a process, such as malware.exe with PID 1234, is created, the functions CreateProcessA/W and NtCreateProcess are executed, triggering a system call to the Windows kernel. The kernel then invokes registered process creation notify routines by iterating over the nt!PspCallProcessNotifyRoutines array, which holds pointers to callback functions. These routines include callbacks registered by various drivers. In the image, the red-highlighted entries such as WdFilter.sys and mssecflt.sys represent drivers that are part of EDR systems, specifically for Windows Defender and Microsoft Defender for Endpoint (MDE), respectively. These EDR-specific drivers register callbacks to monitor and respond to process creation events. When a process creation event occurs, these callbacks are triggered, allowing the EDR system to inspect the process’s details, such as its command line arguments, its executable image, its memory usage, and other relevant information. Additionally, the EDR system might inject a DLL into the process’s memory to hook certain APIs, enhancing its ability to monitor and control the process for security purposes. By leveraging these callbacks, EDR systems can effectively detect and respond to potential threats in real-time. This mechanism allows them to perform thorough inspections and take appropriate actions, such as blocking malicious processes, alerting security administrators, or collecting forensic data for further analysis. Ensuring the integrity of these callback routines is crucial for maintaining robust security measures and preventing malicious actors from bypassing detection mechanisms.The PspCreateProcessNotifyRoutine array EDR (Endpoint Detection and Response) systems, antivirus software (AVs), and Sysmon (System Monitor) register callback routines in callback arrays so they get notified when a process or thread is created or when an image is loaded. These callbacks provide additional information that allows these security tools to detect malware at runtime. Patching or disabling these callbacks can blind EDRs, AVs, and Sysmon, preventing them from obtaining critical information about malware activities. Using WinDbg, a kernel debugger, I reversed the kernel to examine a specific callback array called PspCreateProcessNotifyRoutine. This array stores all the process creation notification callbacks registered by various drivers. Security software and EDR systems register their process creation callbacks in this array using functions such as PsSetCreateProcessNotifyRoutine, PsSetCreateProcessNotifyRoutineEx, and PsSetCreateProcessNotifyRoutineEx2. Each of these functions allows drivers to add their specific callbacks to the array, enabling them to monitor process creation events effectively. To get the actual address of the notification routines, I need to perform a bitwise AND operation on the values in the array with 0xFFFFFFFFFFFFFFF8. This operation aligns the addresses correctly. The result of this operation provides the actual addresses of the callback routines.